Hardware tools:
1. A wire crimper is used to crimp the connectors with LAN cables
2. A tone generator/tester is normally used to locate a cable physically by passing signals through a cable and sensing the signals along the cable using a sensitive receiver.
3. A media tester is used to test a cable for connectivity, loss etc.
4. A patch panel is used to connect incoming and outgoing lines of a LAN. It allows circuits to be arranged neatly by plugging the cables in a pre-designed fashion.
5. Time Domain Reflectometer is used to locate cuts or breaks in a cable.
6. Wire snips are tools designed to cleanly cut the cable.
7. Wire stripper tool is designed to remove the sheathing from a cable to expose the inner wires and to make sure that a clean contact can be made.
8. Cable crimper can be used to attach a connector to the end of a UTP cable.
Network adapter: Following are required while selecting a network adapter.
1. Type of network that it is going to be attached to, e.g.. 10BaseT, 100BaseT etc.
2. Connector type required to attach to the media, i.e. whether it requires RJ-45 / BNC etc
3. Bus type on the Mother board of the computer, e.g.. ISA, EISA, PCI etc.
Whether the driver is provided to support the operating system installed on the computer.
OTDR: OTDR, short for Optical Time Domain Reflectometer can be used for testing a fiber optic cable network. An OTDR injects a short, intense laser pulse into the optical fiber and measures the back-scatter and reflection of light as a function of time. The reflected light characteristics are analyzed to determine the location of any fiber optic breaks or splice losses.
Question: A telecommunications provider has just deployed a new OC-3 circuit at a customer site. You tested the cable from provider end up to the demark using internal loopback and found that the connectivity is present. However, you observed a significant number of dropped packets and errors on the circuit. Which of the following should you do to rule out any problem at the physical layer?
Answer: The problems are most likely to be found by using a loopback plug and an OTDR. OTDR, short for Optical Time Domain Reflectometer finds any problems like nicks in the optical cable. It is used as a troubleshooting device to find faults, splices, and bends in fiber optic cables by displaying the amplitude of the reflected light against time. It works by injecting a series of optical pulses into the fiber under test and extracting, from the same end of the fiber, light that is scattered or reflected back from points along the fiber. Thus, an OTDR can detect light loss and pinpoint trouble areas, making repairs easy.

VOM, short for Volt/Ohm Meter is used with copper cables. Cable tester is typically used with copper cables. Optical cables are immune to electrical noise.
| OC level | Speed |
|---|---|
| OC-1 | 51.85 Mbps |
| OC-3 | 155.52 Mbps |
| OC-12 | 622.08 Mbps |
| OC-24 | 1.244 Gbps |
| OC-48 | 2.488 Gbps |
| OC-192 | 9.952 Gbps |
Punchdown block:
Two types of punchdown blocks used are type 66 and type 110.
Type 66 is an older design used to connect wiring for telephone systems and other low-speed network systems and is not as widely used as type 110. The 66 block has 50 rows of IDC contacts to accommodate 25-pair twisted-pair cable. Block 66 was used primarily for voice communication. Although it was approved for Category 5 and greater, it is not really suitable for anything greater than 10BASE-T due to crosstalk problems. However, there are specialized CAT5e certified 66 blocks available that do meet CAT5e termination standards.
In the network wiring closet, the 110 block is used to connect network cable to patch panels. 110 connections can also be used at the other end of the network cable at the RJ-45 wall jack. 110 blocks are preferred over the older 66 blocks, the 110 block improves on the 66 block by supporting higher frequencies and less crosstalk. Therefore, it supports higher-speed networks and higher grade twisted-pair cable. The termination will be T568A or T568B, depending on which wiring standard is used.
A 110 block is a punch-down block used to connect wiring for telephone systems, data network wiring, and other low-voltage wiring applications. The 110 block improves on the 66 block by supporting higher frequencies and using space more efficiently. A punch-down tool is used to force solid wire into metal slots on the 110 block.
A 110 block is a type of punch block used to terminate runs of on-premises wiring in a structured cabling system. The designation 110 is also used to describe a type of insulation displacement contact (IDC) connector used to terminate twisted pair cables, which uses a punch-down tool similar to the older 66 block.
The figure shows a 110 punch down block tool

Loop-back adapter: It is provided by Microsoft to enable the installation of protocol stack even when there is no Network Interface Card installed. You can also use the loop-back adapter to troubleshoot the problems with the protocol stack, if any, without actually connecting to the network.
Toner probe: A toner probe is a simple cable continuity tester. It consists of two pieces of equipment. One is the tone generator and the other is the probe. One end of the cable is hooked to the tone generator, and the other end is observed for tone using a matching probe. It is also called "fox and hound" wire tracer.
TDR(Time Domain Reflectometer): It is a tool that finds faults in metallic cables like twisted wire pairs and coaxial cables. A similar device, OTDR (short for Optical Time-Domain Reflectometer) is used for testing fiber optic cables.
Fire extinguishers: Fire extinguishers are portable systems. There are four classes of fire extinguishers - A, B, C and D - and each class can put out a different type of fire.
Class A extinguishers will put out fires in ordinary combustibles such as wood and paper
Class B extinguishers are for use on flammable liquids like grease, gasoline and oil
Class C extinguishers are suitable for use only on electrically energized fires
Class D extinguishers are designed for use on flammable metals
Multi-purpose extinguishers can be used on different types of fires and will be labelled with more than one class, like A-B, B-C or A-B-C.
Cable tray : Cable tray is an assembly of metalwork which is used to support insulated electric conductors; similar in function to a metal cable duct, but consisting of a ladder-like metal framework on the bottom and sides, with the top open.
Cable duct: Cable duct is a pipe, either earthenware or concrete, through which prestressing wires or electric cable are pulled.
Command line tools
Some of the important diagnostic commands are explained below
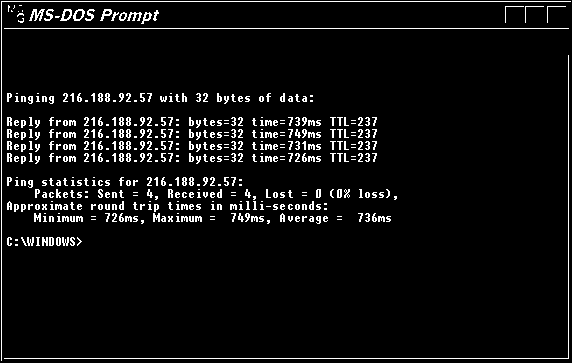
PING: Used to ping the remote system (or the local host) to see that the TCP/IP connection is through. The following fig shows output from ping command.
You can use the ping command to:
Question: You are unable to connect to the remote server on a TCP/IP network from your workstation. You suspect some problem with the installation of your workstation. Which is the preferred sequence of steps for troubleshooting?
Answer: Here, you suspect a problem with the installation of your local work station. The first step would be to make sure that the TCP/IP stack has been installed properly. This can be done by pinging the local host (127.0.0.1). If you are successful, the TCP/IP stack has been installed properly. Now, you can verify the subnet mask by pinging the Default Gateway. If your subnet mask is not configured properly, you will not get a ping reply from the default Gateway. If you are successful, in pinging the default gateway, you can ping the remote server or any intermediate node to check the connectivity.
NBTSTAT: This utility displays current NetBIOS over TCP/IP connections, and display NetBIOS name cache. It Displays protocol statistics and current TCP/IP connections since the server was last booted. NETSTAT is used to review all inbound / outbound connection to a server.
NSLOOKUP: This utility enables users to interact with a DNS server and display resource records.
ROUTE: Used to display and edit static routing tables.
IPCONFIG: Internet Protocol Configuration in Microsoft Windows is a console application that displays all current TCP/IP network configuration values and can modify Dynamic Host Configuration Protocol DHCP and Domain Name System DNS settings.
The following fig shows the output of ipconfig command.

ipconfig /all: Displays the full TCP/IP configuration for all adapters. Without this parameter,
ipconfig displays only IPv6/IPV4 addresses, subnet mask, and default gateway values for each adapter. The command IPCONFIG/ALL shows additional parameters such as host name, DNS servers etc. compared to IPCONFIG command which doesn't show these details

ifconfig (short for interface configuration) is a system administration utility in Unix-like operating systems to configure, control, and query TCP/IP network interface parameters from a command line interface (CLI) or in system configuration scripts. Ifconfig is used to configure and display network interfaces. If no arguments are given, ifconfig displays the status of the currently active interfaces. If a single interface argument is given, it displays the status of the given interface only. If a single -a argument is given, it displays the status of all interfaces, even those that are down.
TRACERT: Used to determine which route a packet takes to reach its destination from source. The tracert utility traces the path to the destination. It is accomplished by controlling the TTL (Time To Live) of the packets in the increments of 1 (one). When the TTL reaches 0, the router sends back an error message saying that the TTL has elapsed. This information is used to find the intermediate devices over the path to destination. Note that some routers may be programmed not to respond to TTL 0 packets. In such event, you may not receive any response.

Tracert and Ping use ICMP as their base protocol. ICMP messages are carried in IP datagrams. The command tracert/traceroute displays the time taken while a packet reach the destination. You will be able to see the time taken by each hop, and identify the faulty link.
The following fig shows tracert command output

Software tools:
Protocol analyzer: Protocol analyzer can be used to capture the packets over a period of time and can be analyzed. It allows you to display the received frames, or generate frames for testing and debugging. It is also possible to create a statistics such as frame size distribution, utilization or protocol statistics. A protocol analyzer is used to monitor and troubleshoot problems such as suspicious activity on the network, verification of network load and type of traffic, artificially injecting load on to a network for the purpose of load testing, and other hard to detect problems with the network.
Certifier, or a certification tester: It is used to examine whether the network complies with ISO or TIA standards as applicable. Some certifiers will also have the capability to test the email, DNS, and DHCP servers for proper response times.
Port Scanner: Port scanner is a device that is used to verify any insecure ports.
The functions of different hardware/software components are:
1. NIC: Stands for Network Interface Card. It is a piece of hardware that interfaces your computer to the external networking media. It sits in one of the slots (eg. PCI slot) on your computer motherboard.
2. NIC driver: NIC driver is responsible for interacting with the operating system and the NIC hardware. Normally, the NIC hardware manufacturer provides the NIC driver software.
3. Operating System (OS): Operating System means Computer OS. For example, Windows XP is a Computer Operating System.
4. Network Operating System (NOS): Network operating system interacts with the Computer operating system, and the network resources. Sometimes, both Computer OS and the Network OS may be combined. An example is Windows 2000 Server. It has both Computer OS as well as Network OS built into the Server OS. An example where the Network OS is installed separately is Novell Netware OS. The Network OS sits separately on a computer and interacts with client computers running different Operating Systems such as Windows XP etc
Bandwidth shaper: as the name implies, provides monitoring and controlling of network bandwidth usage.
Netstumbler: can be used to sniff wireless networks during war-driving. The software tool provides several details of a wireless network such as SSID.
Personal firewall: A personal firewall is software that resides on the end users computers. This is different from a regular firewall, in the sense that a personal firewall is geared to protect a single user computer.
Server rail racks: These are the rails that hold the servers within the rack.
Two-post racks: As the name implies, the servers are attached to the rack system at two locations (one on each side).
Four-post racks: The servers are attached to the rack system at four locations (two on each side).
Free-standing racks: can remain in the appropriate upright position on its own without help from external forces or without being bolted or attached to the wall.
Wi-Fi Analyzer: As more networks go wireless, you need to pay special attention to issues associated with them. Wireless survey tools can be used to create heat maps showing the quantity and quality of wireless network coverage in areas. They can also allow you to see access points (including rogues) and security settings. These can be used to help you design and deploy an efficient network, and they can also be used (by you or others) to find weaknesses in your existing network (often marketed for this purpose as Wi-Fi analyzers).